🚀 Custom Mulesoft Properties Provider Connector for Exchange-Managed Keystores & Truststores! 🔐
Managing keystores and truststores in Mulesoft applications can be a challenge, especially when they need frequent updates. Traditionally, these sensitive files are bundled inside application resources, requiring a redeployment every time they change.
We’ve developed a custom Mulesoft Properties Provider Connector that dynamically loads files from a custom Exchange asset, eliminating the need for manual updates within the application!
📌 How It Works
✅ Instead of storing keystores (.p12) or truststores inside Mulesoft application resources, our connector fetches them dynamically from Anypoint Exchange.
✅ At startup, the connector downloads and unpacks the latest stable version of an Exchange asset into the CloudHub worker’s temp directory.
✅ Files can be referenced locally, allowing Mule to load keystores and truststores dynamically.
⚙️ Key Features
🔹 Exchange-Managed Security Artifacts – No need to store keystores/truststores inside Mule apps. Manage them centrally in Exchange.
🔹 Dynamic Asset Loading – Fetches and extracts the latest version of a specified Exchange asset at runtime.
🔹 Secure & Configurable – Requires authentication using Connected App credentials with Exchange read permissions.
🔹 Flexible Deployment – Supports different Anypoint Platform hosts (default: US Commercial, but can be customized for GovCloud or other instances).
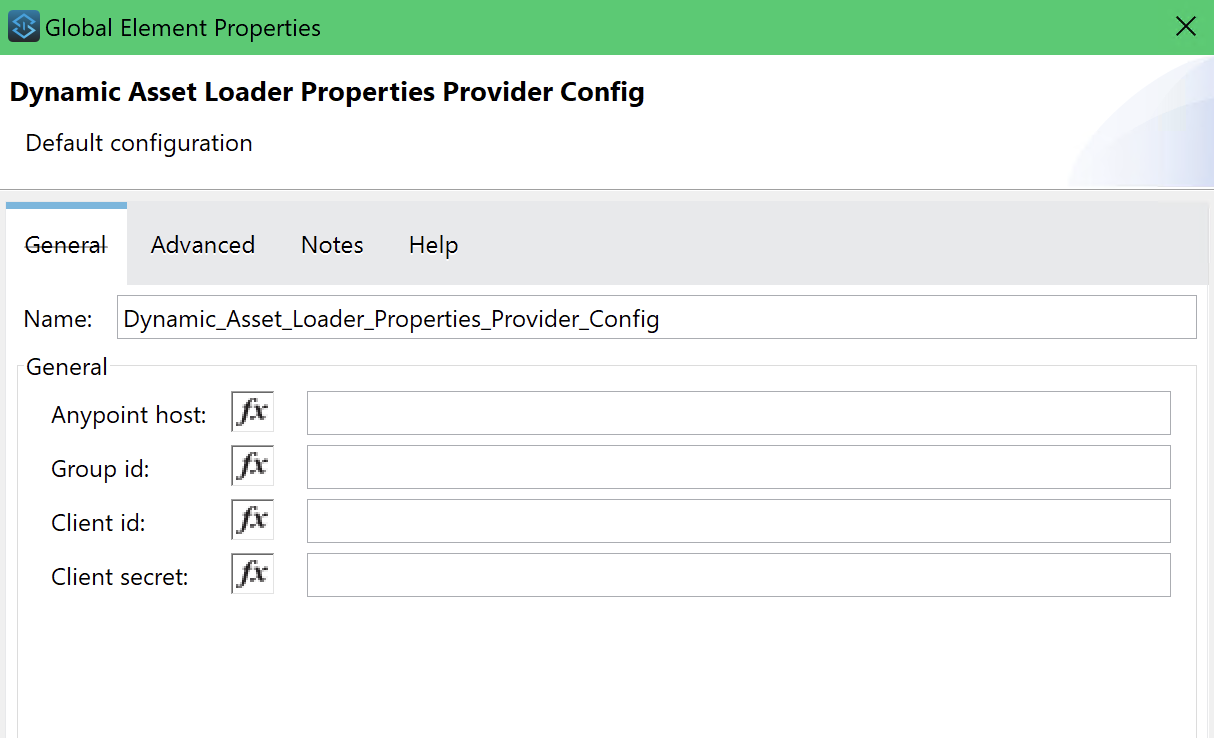
🔑 Required Configuration Parameters
To access Exchange assets, the connector requires:
✔ Connected App Client ID
✔ Connected App Client Secret
✔ Group ID (Organization ID where the asset is stored)
✔ (Optional) Anypoint Host (Default: anypoint.mulesoft.com)
📌 Example Use Case: Loading a TLS Asset
In this example, we dynamically load “myapp-asset-tls” from Exchange. The asset is a .zip archive containing a tls folder with environment-specific keystores:
📂 tls/
├── dev.p12
├── uat.p12
├── prod.p12
During application startup, the asset is downloaded, extracted, and stored in the CloudHub temp directory, making it accessible as a local file.
Here’s how it’s configured in MuleSoft:
<dynamic-asset-loader-properties-provider:config name="Dynamic_Asset_Loader_Properties_Provider_Config"
doc:name="Dynamic Asset Loader Properties Provider Config" />
<tls:context name="https-tls-context" doc:name="TLS Context">
<tls:trust-store />
<tls:key-store type="pkcs12" path="${dynamic-asset::myapp-asset-tls/ssl/@(env).p12}"
alias="${tls.keystore.alias}"
keyPassword="${secure::tls.keystore.keyPassword}"
password="${secure::tls.keystore.password}"/>
</tls:context>
📌 The keystore path is dynamically resolved as:
➡ ${dynamic-asset::myapp-asset-tls/ssl/@(env).p12}
(For example, dev.p12 for dev, uat.p12 for uat environments)
🚀 Why This Matters
🔹 No More Manual File Management – Security artifacts are centrally managed in Exchange.
🔹 Zero-Downtime Keystore Updates – Change keystores/truststores without redeploying the application.
🔹 Enhanced Security – Removes sensitive files from the codebase and application resources.
This is a game-changer for teams looking to streamline TLS/SSL certificate management in Mulesoft applications. 🌟
💬 What do you think about this approach? Would you like to see more dynamic asset management solutions for Mulesoft?